
Understanding perimeter risk arising from external communications
The IC MasterClass team
1 May 2024
Communication in the modern era is fast, freeflowing and viral, and the regulations around how financial services firms communicate with their clients and prospective clients, including the public at large, are not as simple as they first appear.
One critical but often poorly understood part of managing external communications is the concept of perimeter risk: or the risk that a firm's unregulated activity strays into the regulated sphere, resulting in regulatory obligations being missed. Perimeter risk requires constant vigilance to manage, especially in communications, where there are potentially severe consequences for inadvertently providing a financial promotion or investment recommendation.
We discuss the nature of this risk and provide resources to aid firms in their understanding and risk management.
[Ten minute read]
What is perimeter risk?
Perimeter risk exists when a firm's unregulated activity unintentionally strays into the regulated sphere, and the obligations attached to that activity are missed, resulting in potentially severe regulatory breaches.
The risk heightens when firms do not control changes to their activities nor fully understand the extent of their activity universe. It may be created when a firm undertakes regulated activity for the first time, or when a regulated firm expands its business activity into a new market, geography, client segment or product. The less a firm has central oversight of its activities, the more likely it is that a pocket of activity may unintentionally evolve and breach the regulatory perimeter without the appropriate restrictions or controls in place.
Perimeter risk can also result from changes in regulatory expectation or law that redefine what is, and is not, a feature of regulated activity. For example, in 2016 an exemption from the then Market Abuse Directive was removed which meant short term market commentary, for the first time, was to be treated as an investment recommendation, and in 2023 the FCA changed the rules on financial promotions to cover crypto assets.
Perimeter risk is dependent on:
- Whether the firm's activities evolve over time, and if that evolution brings them closer to or over the line of what is regulated,
- Whether a firm’s activities are complex, extensive and decentralised, and are therefore challenging to comprehensively review at any given point in time,
- Whether regulatory guidance (or black letter rules) changes over time, moving the perimeter, and
- Whether the firm's knowledge of the existence of the perimeter degrades, through loss of staff or poorly controlled processes.
If a firm lacks the systems and controls to manage these elements, it is inevitable that, over time, new or changing activity will risk breaching the regulatory perimeter, resulting in potentially severe consequences by way of public sanction, fine or loss of licence.
Critical controls include:
- Total capture activity mapping that is subject to regular review,
- New activity approvals and change management stop/go decisions that enable perimeter risk to be evaluated,
- Robust regulatory change management and horizon scanning systems,
- Regular training campaigns on the nature of perimeter risk, and
- Connectivity between businesses and regulatory experts.
Even for firms that have a simple and mature product offering, perimeter risk can creep in with external communications. Modern technology makes communicating with clients, the public, shareholders and suppliers easy, and expressing an opinion to a client or the general public can unintentionally become marketing or an investment recommendation, triggering a gamut of obligations and creating significant risk for any firm. We explain this in detail below.
The communications perimeter
Communications regulations are built on principles of being 'clear, fair and not misleading' and 'caveat emptor', or 'buyer beware’, focusing on rules that control content, and rules that control disclosure about content. They apply when the content, in effect, attempts to, or is capable of, persuading the reader to pursue a financial action.
Secondary rules regarding the sharing of ‘anything of value’ as an inducement - be it a quid pro quo arrangement with a government official or to entice a client into a trading relationship - also bite when premium content is offered for free, and record keeping obligations apply when certain information is provided to a client or prospective client.
Whilst the rules appear simple in principle, they are complex in practice: they differ depending on author, content, purpose, audience and distribution channel, and as communication channels evolve and social media becomes ever more prevalent, so too does the potential damage to a firm's reputation or harm to a client. The harm goes beyond misrepresentation: it also stems from potential breaches of confidentiality and data misuse, bribery, front running inside information and mismanaging firm and employee conflicts of interest.
What triggers the perimeter?
On the regulatory side of the perimeter are communications that have a call to action, an invitation to enter into financial services activity, or an investment recommendation. These types of communications are typically subject to a number of regulatory disclosures and content controls, in order to protect the audience from being misled, and may also be subject to pre-filing requirements or pre-review by a qualified analyst. Independently produced and distributed research, which can demonstrate separation from other areas of the firm that may otherwise wish to influence it for their own ends (typically, investment banking and markets sales), has an additional tier of rules to comply with.
Content is the primary, but not sole, determinant of whether a communication triggers the perimeter. For example, in the UK, an invitation or inducement to engage in investment activity triggers the Financial Promotions Order (2005). A secondary determinant is audience: in the US, any communication with retail clients, including the public, triggers FINRA rule 2210, however exemptions apply if the content does not have a financial or investment recommendation in them. Communications to retail face more restrictions in order to protect vulnerable customers, and may prohibit the distribution of marketing related to high risk investments.
There are also a number of administrative and factual communications with clients that must comply with regulatory obligations, for example client agreements, contract notes and performance reviews, and securities and fund prospectuses. Such communications are straightforward to identify and generally controlled through the use of approved templates and distribution channels, and may be embedded in automated processes.
What types of communication could cause perimeter risk?
Firms build credibility through thought leadership, and relationships through generating ideas. They often offer ‘education’ materials and market insights, or events unrelated to specific investment ideas, in order to remain close to clients. Their PR departments build ‘branding’ independent of specific client services or investment recommendations. These activities can fall outside of the sphere of regulated activity, even though it is a regulated firm doing them, on the basis there is no solicitation of or call to action regarding a specific investment strategy or activity, but the line - the perimeter - is not so black and white. Even if there is no underlying recommendation of something to buy, sell or do, if the purpose for which they are created is to generate leads for a particular service or investment, especially if a reasonable investor acts as a consequence of receiving the communication, a case can be made that there was an implicit invitation or recommendation within it.
Like most compliance challenges, much of the problem is definitional. As part of its consultation with the industry on the Market Abuse Regulation, the FCA stated it considered there to only be three types of client communication: fact, personal recommendation (advice), or investment recommendation. By design, thought leadership is none of these things.
There is an implicit assumption that a firm is, in the words of Glengarry Glen Ross, 'always closing’. It is not simply the content that matters, but also the independence of the author from the firm’s sales division, the intent behind the publication of the piece, and the reasonable expectation of an investor - simply declaring a piece is not an investment recommendation does not make it so. To credibly make the case that thought leadership is not a financial promotion or marketing effort, a degree of separation, or clear water, needs to be evidenced between the departments producing thought leadership content and departments focused on sales activity (both on the public and private side of the firm). This separation needs to be clearly articulated in firm policy and explain when a firm considers its communications to be outside the regulatory perimeter, and how it polices that line.
Breaching the communications perimeter
Unknowingly sending a regulated communication can have potentially severe consequences. Breaches can include:
Failing to demonstrate that content with a financial promotion or call to action is clear, fair and not misleading and failure to label the content as marketing. There are prescriptive obligations as well as principles to comply with and firms must demonstrate its systems and controls are fit for the purpose of identifying and reviewing such content. Content will also need to comply with broader advertising standards;
Content that may be appropriate for an institutional audience may be prohibited, or more tightly controlled, if sent to retail clients, including being made publicly available, especially if it focuses on high risk investments or other content deemed unsuitable for retail;
Sending an investment recommendation externally without appending a specific suite of conflict of interest disclosures is a breach of the Market Abuse Regulation and may result in censure or financial penalty, especially if it appears to have impacted the price of the financial instrument in question;
Comprehensive disclosure rules exist in numerous jurisdictions, and firms need to comply with their domestic rules as well as those of the jurisdictions they distribute content to. This is a particularly challenging issue for content published on a public-facing website, which can be accessed by clients in any country;
Unregulated firms that publish opinions and recommendations on buying financial instruments, funds, or financial services risk breaching licencing regulations depending on the jurisdiction that the content is created and distributed in, especially if they are sent cross-border;
Providing content to a government official that is deemed to be ‘something of value’ in a quid pro quo arrangement may be seen as bribery;
Providing content to a portfolio manager that is deemed to be ‘something of value’ without charging an unbundled price for it may breach Inducement rules;
Including sensitive, confidential or personally identifiable information in a publication without first confirming it is appropriate to share publicly, especially if it is being shared selectively, may breach GDPR or disclosure and transparency regulations; and
Circulating content that rises to the level of a financial promotion, market commentary, investment recommendation, research or call to action without making a record of it is a breach of record keeping regulations in multiple countries, and using an unmonitored channel to communicate with clients will likely incur significant regulatory penalty (see the recent spate of fines for WhatsApp use for more colour).
Managing communications perimeter risk
There is no definitive answer for how to structure one's communications control environment, as it will depend on the firm's risk appetite.
A risk averse firm can manage communications perimeter risk through requiring all external communications to be vetted and switching off external email for individuals unless they are on an approved list, but there are significant costs to this. It can tie up limited risk resource performing unnecessary reviews. AI checklists may be a viable solution, but these require investment, and triage when more complex reviews are needed.
Centralising control is disruptive to the quick and free flow of information, and can have significant commercial impact, but delegating reviews to business leads could result in inconsistency and error.
A more pragmatic alternative is to have a centralised repository of specific communications that have been approved for external dissemination and appropriately watermarked. This can enable content to be labelled as ‘internal use only’ or ‘approved for external dissemination’, or ‘approved for distribution to institutional clients only’ and in essence certifies the content as fit for external distribution, enabling greater transparency and oversight.
A firm could, as a matter of policy, treat all communications as ‘marketing’ and subject them to the full suite of regulatory disclosures and checks, but it will likely be over-disclosing; something that can result in criticism and confusion, as well as unnecessarily slowing down publication. In order to comply with dynamic disclosures relating to conflicts of interest, for example, content needs to go through a publishing tool; there are simply too many nuanced obligations that change daily, such as a firm’s position in a named stock.
A degree of customisation in controls is necessary; subjecting all communications indiscriminately to the same control environment will inevitably result in poorer commercial outcomes, administrative cost and may also reduce competitiveness, especially if all content needs to go through a checklist before it can leave the firm.
Firms could target pre-review on higher risk communications and periodically review which communications should be considered so. This requires comprehensive understanding as to what communications the firm produces, for what purpose, and to whom it distributes them. The 'total capture' of communication types and teams that are authorised to send them is a practical challenge; an inventory needs to be kept up to date, requiring period firm-wide communication audits.
Absent external email blocks, the success of the communications control environment largely comes down to culture: if individuals are used to acting independently, they will continue to share their ideas with clients, the media and the public, especially in the pursuit of generating alpha or impressing their expertise. Reward and disciplinary structures need to be properly aligned in order to ensure workers follow the set practice and do not continue to engage clients through their own methods.
A firm also needs to be on top of its horizon scanning and ensure no new or amended communication channels or publication suites are authorised without first being reviewed for perimeter risk, and to ensure that changes in thinking - be they legal, regulatory or societal - are captured in the firm's live view of the perimeter.
Common understanding of the perimeter is vital to ensure that individuals involved in processes on the unregulated side of it are fully aware of the trip hazard.
The IC MasterClass Cheatsheet
The IC MasterClass Cheatsheet is a resource that consolidates the themes discussed in this article.
If you would like to arrange a curated IC MasterClass on the topic of perimeter risk, please contact us today.
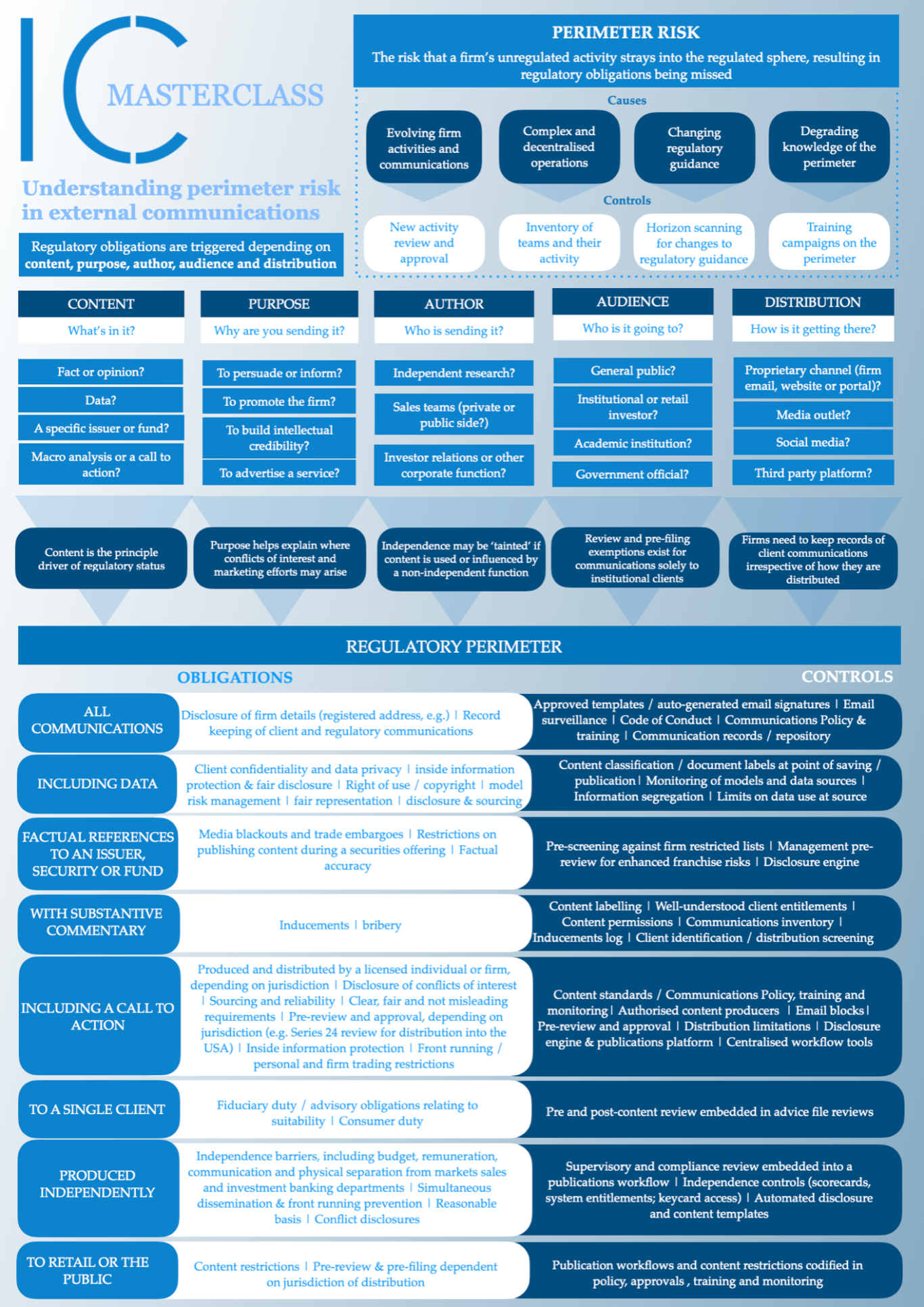

- Perimeter risk is the risk that a firm's unregulated activity strays into the regulated sphere, resulting in regulatory obligations being missed
- Perimeter risk is heightened in firms that are complex, decentralised and changing, and do not maintain sufficient institutional knowledge of what the perimeter is and how it may be changing
- Perimeter risk can be controlled through comprehensive and regularly reviewed activity mapping, new and changing activity approvals, horizon scanning and regulatory change management systems, and training campaigns focused on raising perimeter awareness
- External communications can pose a significant perimeter risk, especially if a firm utilises ‘thought leadership’ or ‘educational materials’ and its staff are unaware of the complexity of factors - author, intent, audience, distribution and content - that determine if and how the content is regulated
- If a communication accidentally trips the regulatory perimeter, it may breach regulations relating to disclosure, conflicts of interest, consumer duty, pre-filing, content restrictions, bribery and data privacy
- The communications regulatory perimeter is not clear cut: the definition of an ‘implicit’ recommendation is open to judgement and a firm’s position on it can be criticised
- Controls to manage perimeter risk arising from the sending of external communications will vary dependent on a firm’s risk appetite, and need to finely balance the commercial impetus for speed to market and client service with the risk of regulatory breaches
- A risk-based approach requires comprehensive mapping of the communications a firm sends, to whom and for what purpose, and robust approval processes for new publications
- These controls need to be plugged into wider firm activity checks and approvals in order to ensure new communications do not fall under the radar of the experts who can identify perimeter risk with them
© Copyright Innovate Compliance Limited | All rights reserved | Reproduction or commercial use of any of the content on this site or other IC materials is prohibited without the express permission of Innovate Compliance
Innovate Compliance Limited is a UK registered company | number 15523445 | 63-66 Hatton Garden, Fifth Floor, Suite 23, London, England, EC1N 8LE
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.
